New - Role Based Access Control for Applications
Overview
By default, once the Preserve365 Outlook application is consented, it can access all mailboxes in your Microsoft 365 tenant.
If your organisation prefers to limit which mailboxes Preserve365 can access, you can configure Role Based Access Control (RBAC) for Applications in Exchange Online.
This allows you to specify exactly which mailboxes the Preserve365 Outlook connector can scan.
This step is optional, but recommended if you want more granular control over access.
For more information, see
Configure Role Based Access Control for Applications in Exchange Online
Purpose
RBAC for Applications lets you restrict the Preserve365 Outlook connector to a defined set of mailboxes.
Any attempt by the connector to access mailboxes outside that scope will be blocked by Exchange Online.
Prerequisites
-
Exchange Administrator permissions
-
Exchange Online PowerShell module
-
The Preserve365 Outlook App ID (Client ID) from your Microsoft Entra (Azure AD) tenant
Steps
1. Identify the Preserve365 Outlook App’s Client (Application) ID
-
In the Azure Portal, go to Microsoft Entra ID → App registrations
-
Locate the registration for the Preserve365 Outlook connector
-
Under the app’s Overview section, copy the Application (client) ID
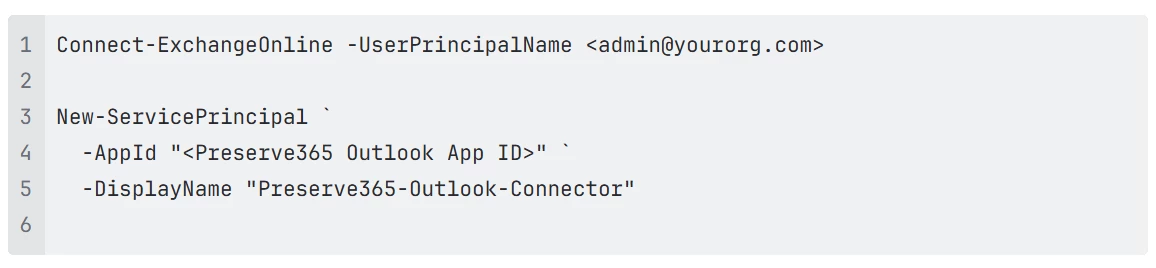
2. Register the Service Principal in Exchange Online
Connect to Exchange Online PowerShell and create a service principal that represents the app in Exchange Online:
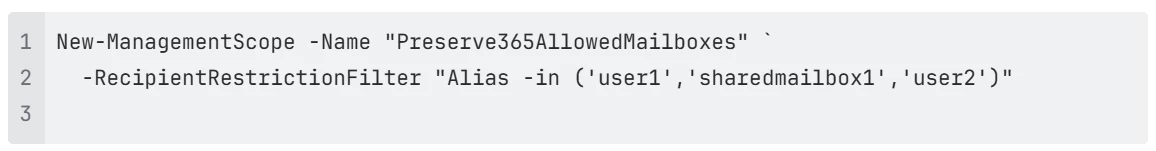
3. Define the Management Scope
Create a management scope to specify which mailboxes the connector can access.
For example, to limit access to specific mailboxes:
You can filter by other attributes such as PrimarySmtpAddress, Department, or CustomAttribute1.
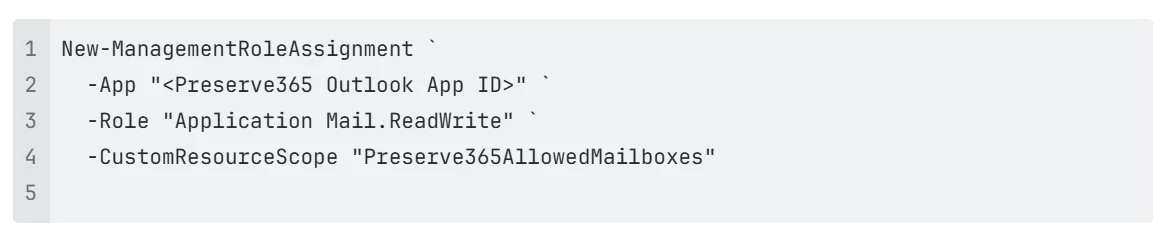
4. Assign Application Roles to the Preserve365 Outlook Connector
Assign the required application roles (permissions) to the Preserve365 service principal, scoped to the mailboxes defined above.
Example:
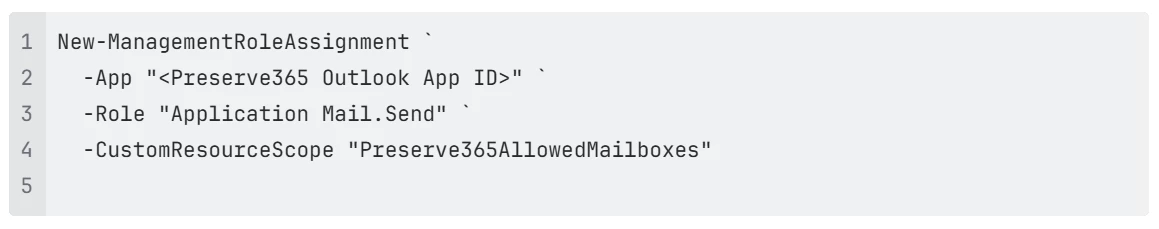
If you also need send permissions, run:
5. Verify the Configuration
Run the following command to confirm the role assignments:
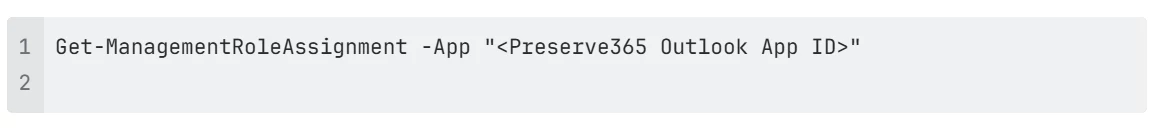
You can also use:
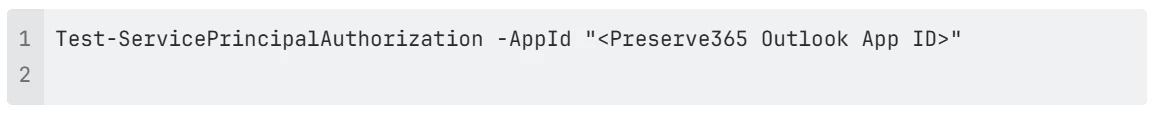
to validate that the connector can access mailboxes only within the defined scope.
Changes may take up to one hour to fully propagate.
Managing Access
To change which mailboxes the connector can access:
-
Add access: Update the management scope filter to include additional mailboxes.
-
Remove access: Update the scope to exclude mailboxes or remove the role assignment.
All changes are applied automatically by Exchange Online once replication completes.
Summary
Using Role Based Access Control for Applications ensures that the Preserve365 Outlook connector operates with the principle of least privilege —
granting access only to approved mailboxes while maintaining full compliance with Microsoft’s latest security standards.
Old - Application Access Policies (legacy) version
By default, once the Preserve365 Outlook application is consented, it can access all mailboxes in your Microsoft 365 tenant.
If your organisation prefers to limit which mailboxes Preserve365 can access, you can create an Application Access Policy in Exchange Online. This allows you to specify exactly which mailboxes the Preserve365 Outlook connector can scan.
This step is optional, but recommended if you want more granular control over access.
For more information, see Application Access Policies (legacy)
Purpose
An Application Access Policy restricts the Preserve365 Outlook connector to a defined group of mailboxes. Any attempt to access mailboxes outside that group will be blocked by Microsoft Graph.
Prerequisites
-
Exchange Administrator permissions
-
Exchange Online PowerShell module
-
The Preserve365 Outlook App ID (Client ID)
Steps
-
Identify the Preserve365 Outlook App’s Client (App) ID
Locate the App (Client) ID of the Preserve365 Outlook connector in your Microsoft Entra (Azure AD) tenant:
-
In the Azure Portal, navigate to Azure Active Directory (Entra ID) → App registrations
-
Find the registration corresponding to the Preserve365 Outlook app
-
Under the app’s Overview or Essentials section, copy the Application (client) ID Microsoft Learn+2Microsoft Learn+2
-
Create a mail-enabled security group in Entra ID
In Entra ID (Azure AD), create a new mail-enabled security group.
Add any users or shared mailboxes that you want Preserve365 to access. -
Create the Application Access Policy
In Exchange Online PowerShell, run the following command: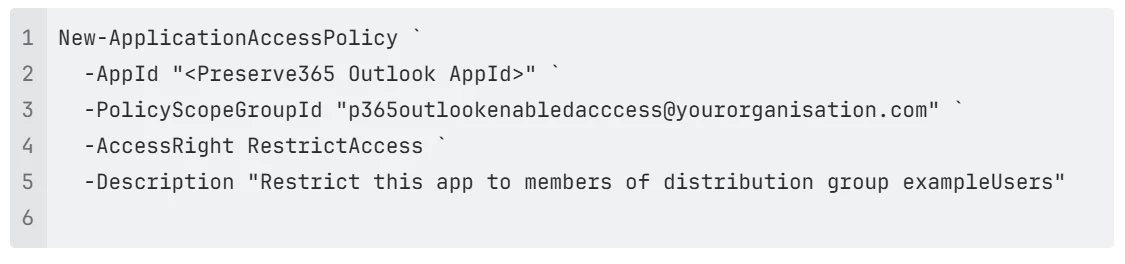
- Verify the policy
To confirm the policy was created, run:

Managing Access
Once created, this policy ensures that the Preserve365 Outlook connector can only access the mailboxes listed in your Entra ID security group.
To grant or revoke access, simply add or remove mailboxes from that group.
Changes typically take effect within one hour.
